Examples
Minimus images are often used in multi-stage builds. Below are a list of recommended tutorials to help you get started:Advantages of a multi-stage build
Using a different base image for the builder stage and the runtime stage has several advantages:-
The dev image contains more packages and is therefore more likely to contain more vulnerabilities. For example, we can see that the Python production image has fewer vulnerabilities than the Python dev image.
This behavior is consistent across all images, where many times the production image is completely free of vulnerabilities but the dev image might have a few.
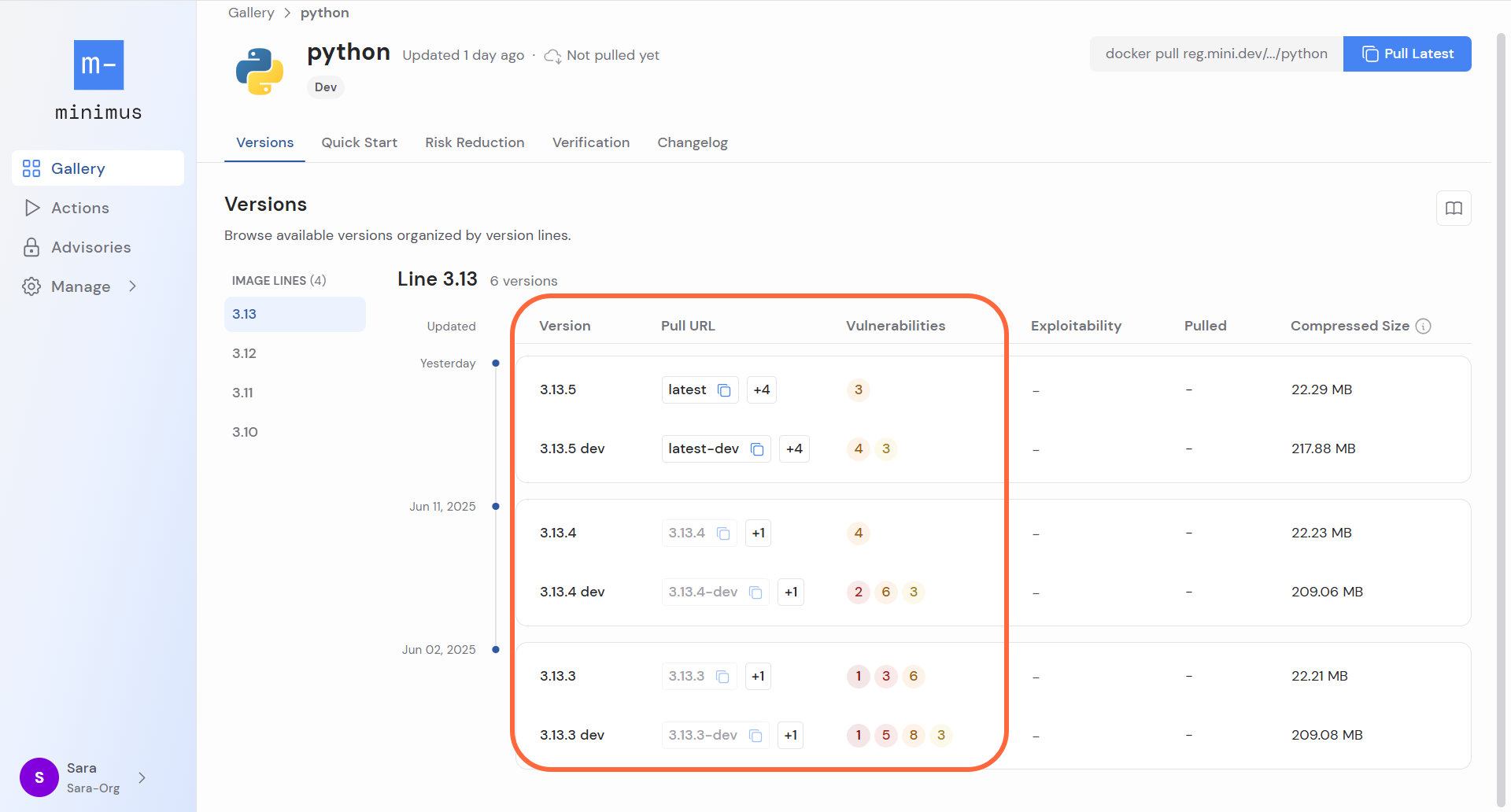
-
When building an app, there is no advantage to including dev packages that increase the attack surface and are not required to run the app. It is preferable to build the application in stages and reduce the final image in size and attack surface. As a result, the final image will have a small attack surface and fewer vulnerabilities, if any.
Just to get a sense of the size differences, the compressed size of the python image is just over 22 MB - compared to 218 MB for the python dev image. Similarly, the SBOM for the Python production image lists 23 packages while the Python dev image lists 73 packages.python:3.13.5 python:3.13.5-dev Compressed size 22 MB 218 MB SBOM packages 23 73
When to use a multi-stage build
Basically, you should use a multi-stage build whenever the opportunity presents itself.- Any compiled or interpreted language is a good candidate for a multi-stage build. This includes (but is not limited to): Python, NodeJS, Rust, PHP, Ruby, etc.
- Go is a special case as you can run the compiled binary on a minimal runtime base. Learn how to run a Go app on a runtime base
- Some images come in building pairs that have different names. For example:
- The Dotnet SDK image is often used as the builder in combination with the ASP.NET image for the runtime stage.
- OpenJDK is often used for building Java applications while OpenJRE (open-source Java Runtime Environment) is used to run them. See our Java quick start tutorial