Affected images only refer to production images. Development image variants (for example, an image tagged
latest-dev) are excluded by default.Refer to version-specific vulnerability reports for information about vulnerabilities affecting development images. Learn moreOverview
Before you dive into the details, the advisories page top section shows helpful metrics about the advisories published for Minimus images:- Total number of new vulnerabilities detected in the past 7 days in Minimus images
- Total number of vulnerabilities detected over the past year in Minimus images that are currently known as active exploits (i.e. they are on the CISA KEV list)
- Total number of vulnerabilities detected over the past year in Minimus images that are currently labeled as likely exploits (i.e. they have a high EPSS probability score and are likely targets for exploitation).
- Total number of critical severity vulnerabilities detected over the past year in Minimus images.
Advisories table
An advisory is published for every affected origin package. Every advisory lists all affected images and their respective fixed version information.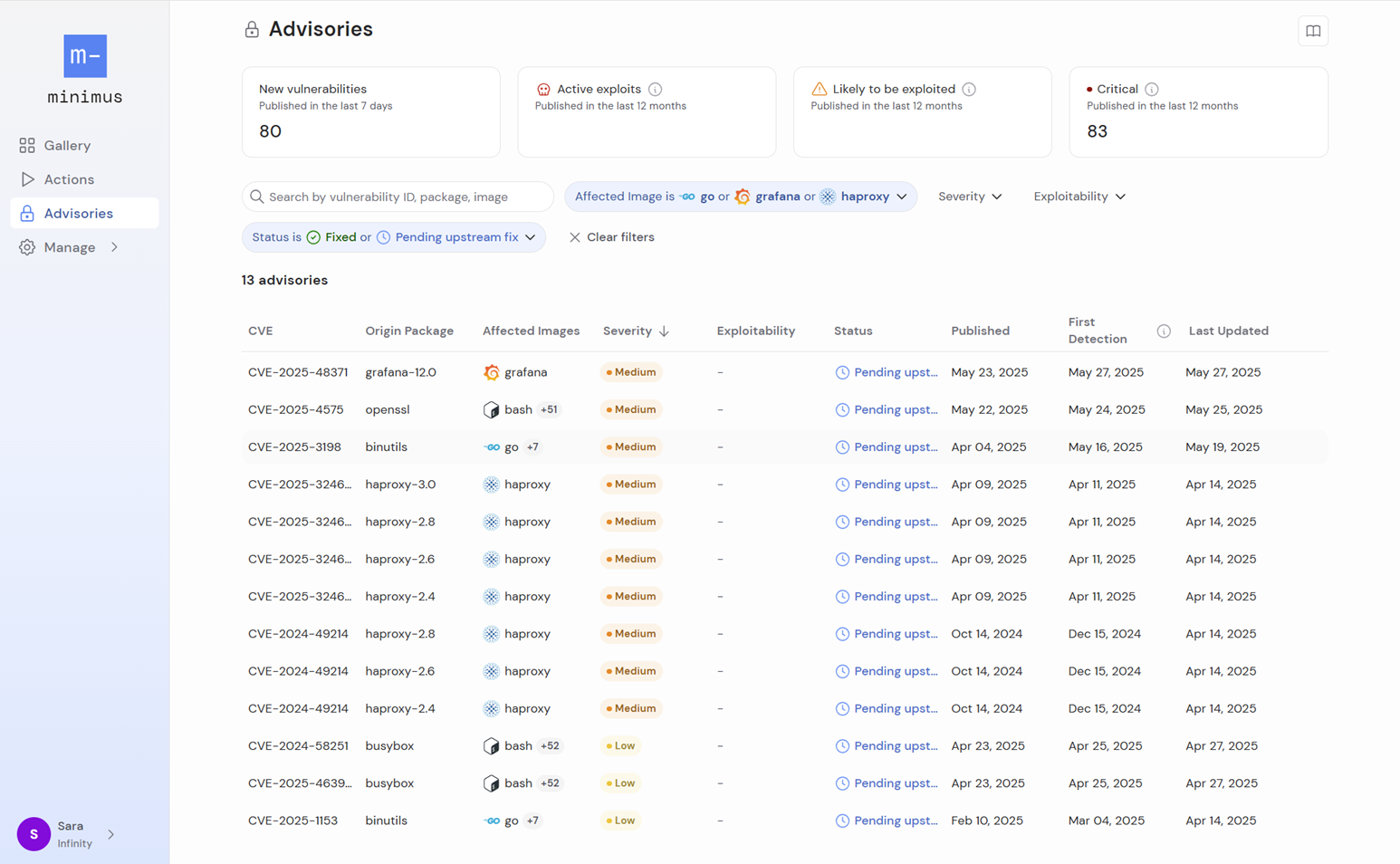
- CVE ID or GitHub security advisory ID
- Origin package affected by the vulnerability. Note that affected secondary packages are detailed in the vulnerability report for specific image versions.
- Affected images (Filtered by default by production images. Excludes dev images, for example
latest-dev.) - Severity as determined by NVD (CVSS score, where the most recent CVSS vector is shown). Learn more
- Exploitability Learn more
- Status
- Date published
- First detection
- Last updated
Drill down on a security advisory
Click on an advisory in the table to view its detailed listing. The advisory shows general information about the vulnerability alongside detailed information listing all affected images, by origin package, and the status history. Learn moreFiltering, searching, and sorting advisories
- Filtering options To help you identify the relevant information quickly, you can filter the advisories list by affected images, severity, exploitability, and status. The filters are friendly UI elements, and do not require complex syntax.
- Search options You can search the advisories by a full or partial vulnerability ID and/or a package and image name. You can of course combine search terms with filtering criteria.
- Sorting options You may sort the advisories by their severity and last update.
Advisory status
| Status | Description |
|---|---|
| Under review | Minimus is following up on the vulnerability report to confirm the report and determine if the vulnerable code affects the package. |
| Affected | The vulnerability was confirmed by the Minimus team to be affecting the package. |
| Unaffected | The vulnerability was determined to be a false-positive by Minimus. Reasoning is provided in a note. |
| Pending upstream fix | Minimus is waiting for the source repo to publish a fix for the package. The image will be patched as soon as the fix becomes available. |
| Fixed | A patch was applied to remediate the vulnerability. |
| Fix not planned | Usually a fix is not planned for package versions that have reached their end of life (EOL). Reasoning is provided in a note. |