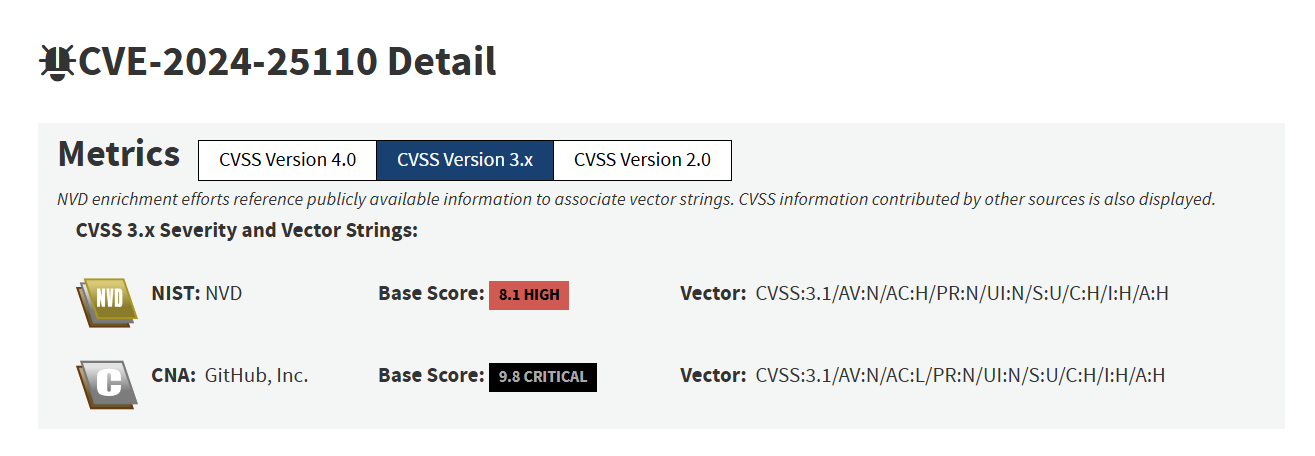
Severity score disputes
The same CVE may be assigned different CVSS scores by different vendors. For example, CVE-2024-25110 was assigned a staggering CVSS score of 9.8 by GitHub, but only 8.1 by NVD. There isn’t as much of a consensus as one might expect. Severity score disputes reflect different environmental assumptions (for example, comparing a publicly exposed server to an internal system behind a firewall) and different assessments of the potential impact, a factor considered to be highly subjective. The timing of the analysis is also significant, with the most recent analysis likely to be the best informed. In general, CVSS scores are rarely revisited or updated.CNA ranking
Vendors officially authorized to publish CVSS scores are known as CNAs, CVE Numbering Authorities. CNAs are evaluated by NVD on an ongoing basis and the CVSS vectors they publish are regularly audited. NVD ranks CNAs according to a measure known as acceptance level (ref). There are 3 acceptance levels, ranked from lowest to highest:- Reference - under evaluation
- Contributor - on track to become a Provider CNA
- Provider - highest confidence, on par with NVD analysts

Primary analysis
When a CVE has been evaluated by more than one authority, Minimus will show the primary CVSS score and vector, as determined by the NVD API. The primary score is not explicitly marked in the NVD CVE listing, but it plays an important role in the NVD API. The determination is as follows:-
Provider CNA analysis takes priority over NVD analysis. For example, CVE-2023-21557 was determined to be 7.5 by Microsoft (Provider CNA) and 9.1 by NVD. The NVD API shows the Microsoft vector as the primary one, and Minimus will show it accordingly.
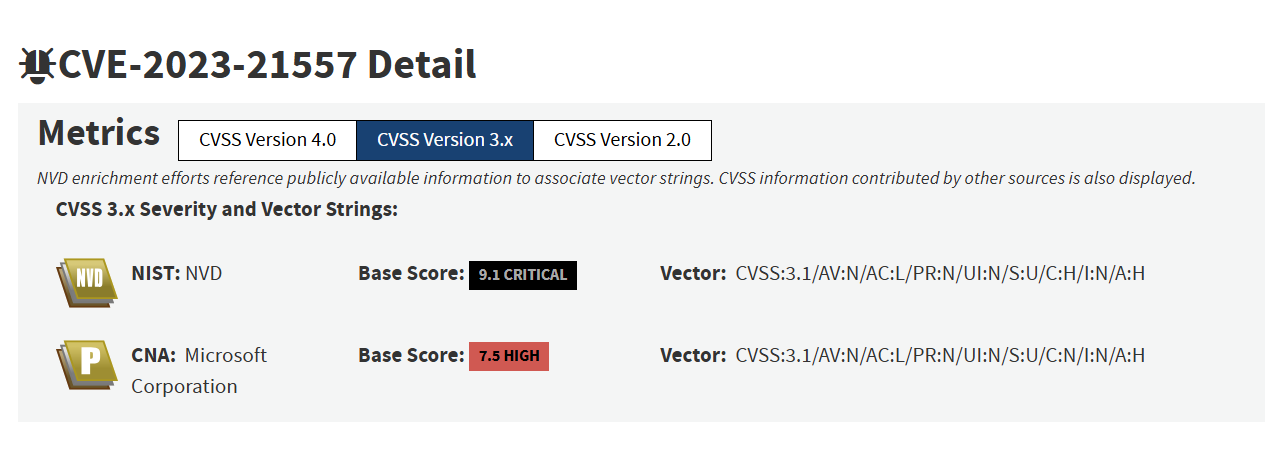
- NVD analysis takes priority in all other cases. (That is, analysis by CNAs at the contributor or reference acceptance levels will never be shown as primary by the NVD API.) For example, CVE-2024-25110 was determined to be 8.1 by NVD, and 9.8 by GitHub (Contributor CNA). The NVD vector is the primary one, and Minimus will show it accordingly.