- Images - Refers to the image type, as in Nginx, Golang, PHP, Redis, etc.
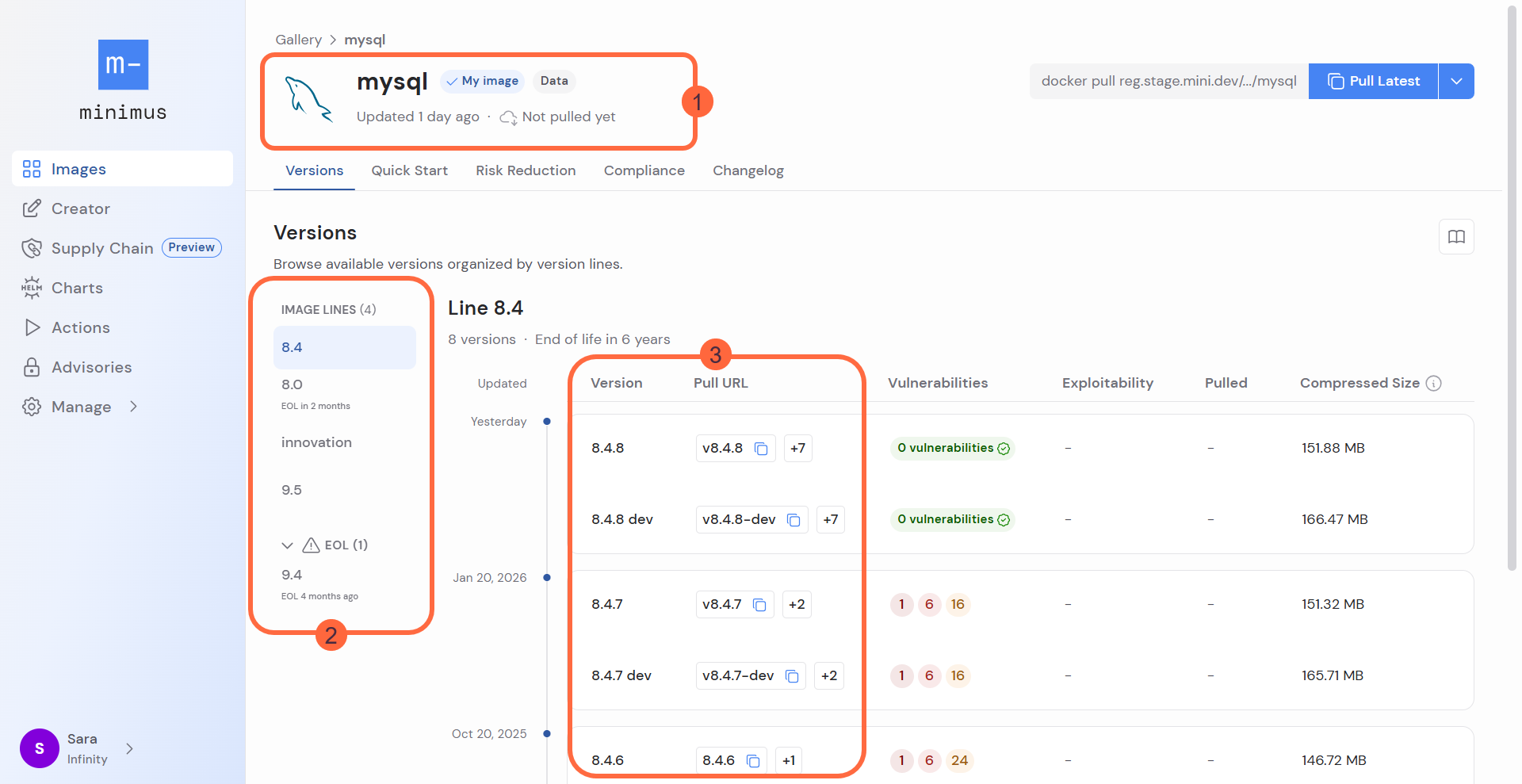
- Image lines - Refers to the release branch. Minimus image lines match the upstream’s maintained release lines.
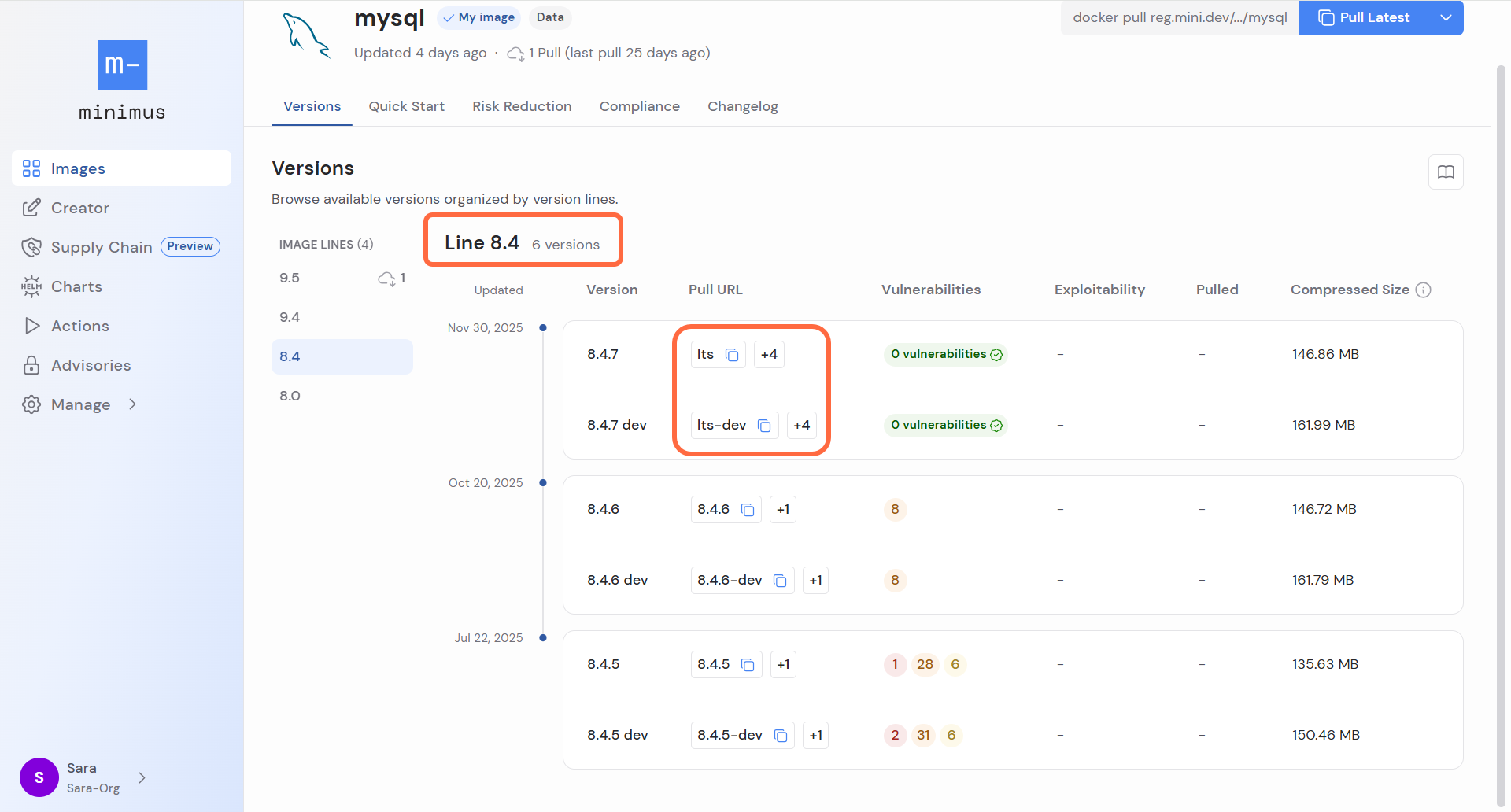
- Image versions - Refers to the exact version number or release number. Image versions are always placed under the appropriate image line.
About image lines
Minimus maintains release lines that are being actively supported by their upstream projects. To be considered actively supported, the line must be receiving bug reports and security issues and putting out version updates. Most projects maintain at least 2 lines, often named. For example:- nginx has a
mainlineand astableline (ref). - MySQL has an
innovationorlatestline and two long term support lines -ltsand the line previously tagged aslts(ref). - Postgres maintains 5 release lines, but they are not named (ref).
- Python maintains 2 active support lines and sometimes another release-candidate -
rc(ref).
mainline, stable, and lts.
About image versions
Minimus follows the release schedule of the upstream projects. Every time a new version is released, Minimus will cut an image of the new version. The version numbers are identical to the upstream project and will be shown in the relevant image line in the Minimus gallery. Learn more about the Minimus new version SLA The image version typically follows semantic versioning conventions in X.Y.Z format (ref). For example, for the nginx image, the latestmainline version is 1.29.3 and the latest stable version is 1.28.0 (on Dec 4, 2025).
Internal package updates
Minimus maintains the most recent version in each image line on a daily basis. Image versions that are actively receiving updates will be rebuilt whenever there are packages to update. These internal updates will not affect the image version, but will be recorded in the image Changelog and the Digest History. Learn more You can also use the unique Timestamp Tag to identify the exact build you are using for an image version. The unique timestamp tag is a human-readable alternative to the image digest developed by Minimus. Learn more about timestamp tags An image line will often contain several image versions, listed chronologically. Minimus recommends that users update their image to the most recent version build as soon as possible to benefit from the vulnerability fixes.End of life (EOL) information
Minimus aims to provide accurate and complete information about support timelines and expected end of life dates for image lines. Note that some upstream projects do not provide the EOL dates. In other cases, the sunset dates may only be announced later on and are not available at the time of the image line release. Where the EOL dates are available, you can use them instead of referring to the upstream project. Learn moreMulti-architecture images
Minimus images are built to support multiple CPU architectures (amd64 and arm64) and can run on different hardware platforms without requiring separate images. When you run thedocker pull command to get an image from the Minimus gallery, it will automatically pull the correct architecture for your system.
Selecting the right image line
If you’re not already committed to a particular image version, you may be asking yourself which image line you should use? Minimus can help you decide based on your requirements:- As a general recommendation, unless you have constraints such as app compatibility issues, you should always use the latest version. This ensures that you are using the most up-to-date version and can benefit from security updates more completely.
- If your testing cycle is relatively longer, you may be forced to use a previous version line. You should still opt for the most recent version within the line to benefit from daily security updates.
- If you have constraints that require you to use an older image version, note that the version will not receive security updates. Minimus images are minimal and hardened from the start and so accumulate vulnerabilities more slowly, thereby staying more secure for a relatively longer period of time.
- Visit the Minimus gallery to view a current vulnerability report for any image version. The report provides an up-to-date status on the vulnerabilities detected in the version. Learn more about image vulnerability reports