General information
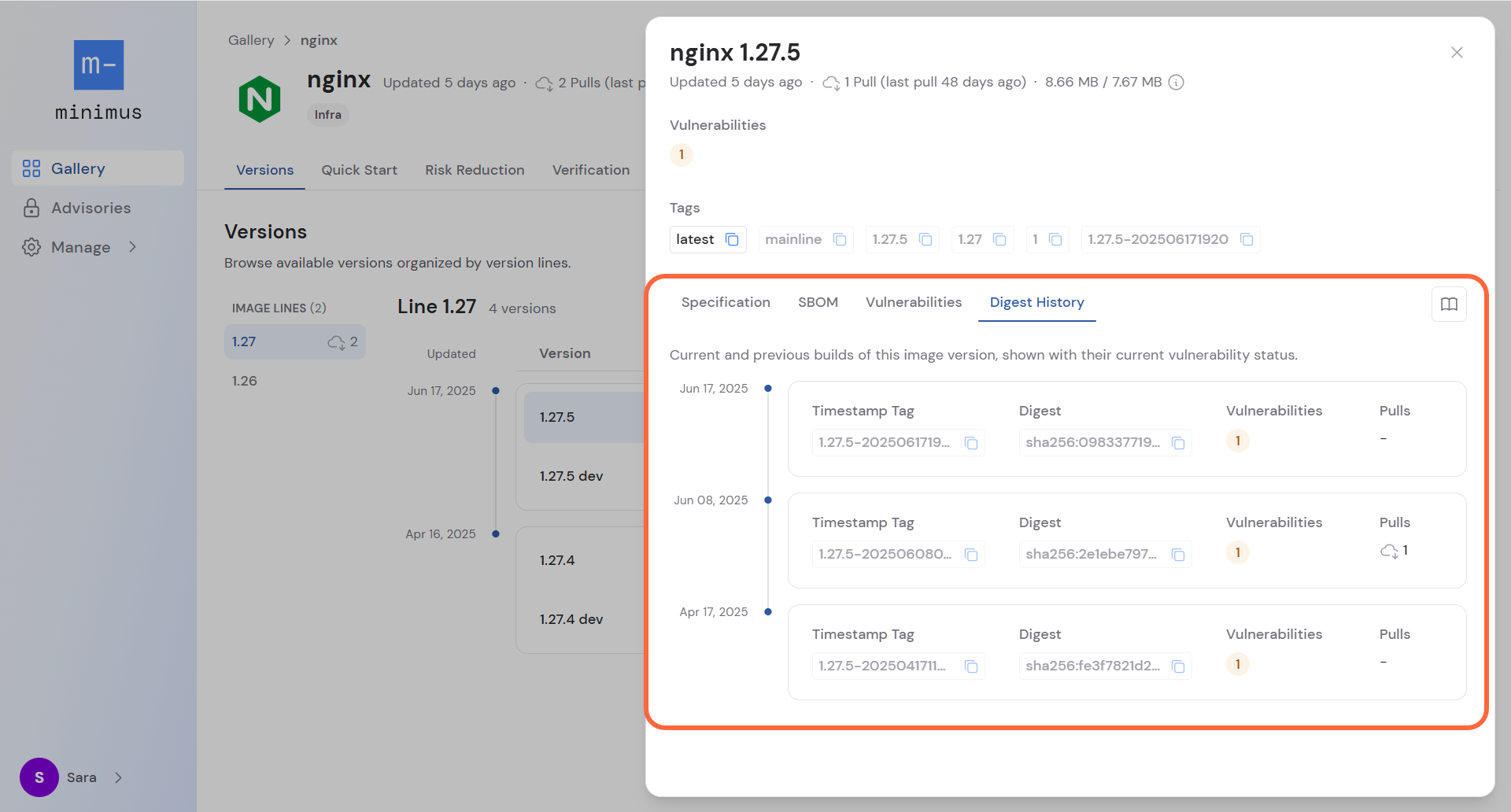
Click any image version in the image line to view its details.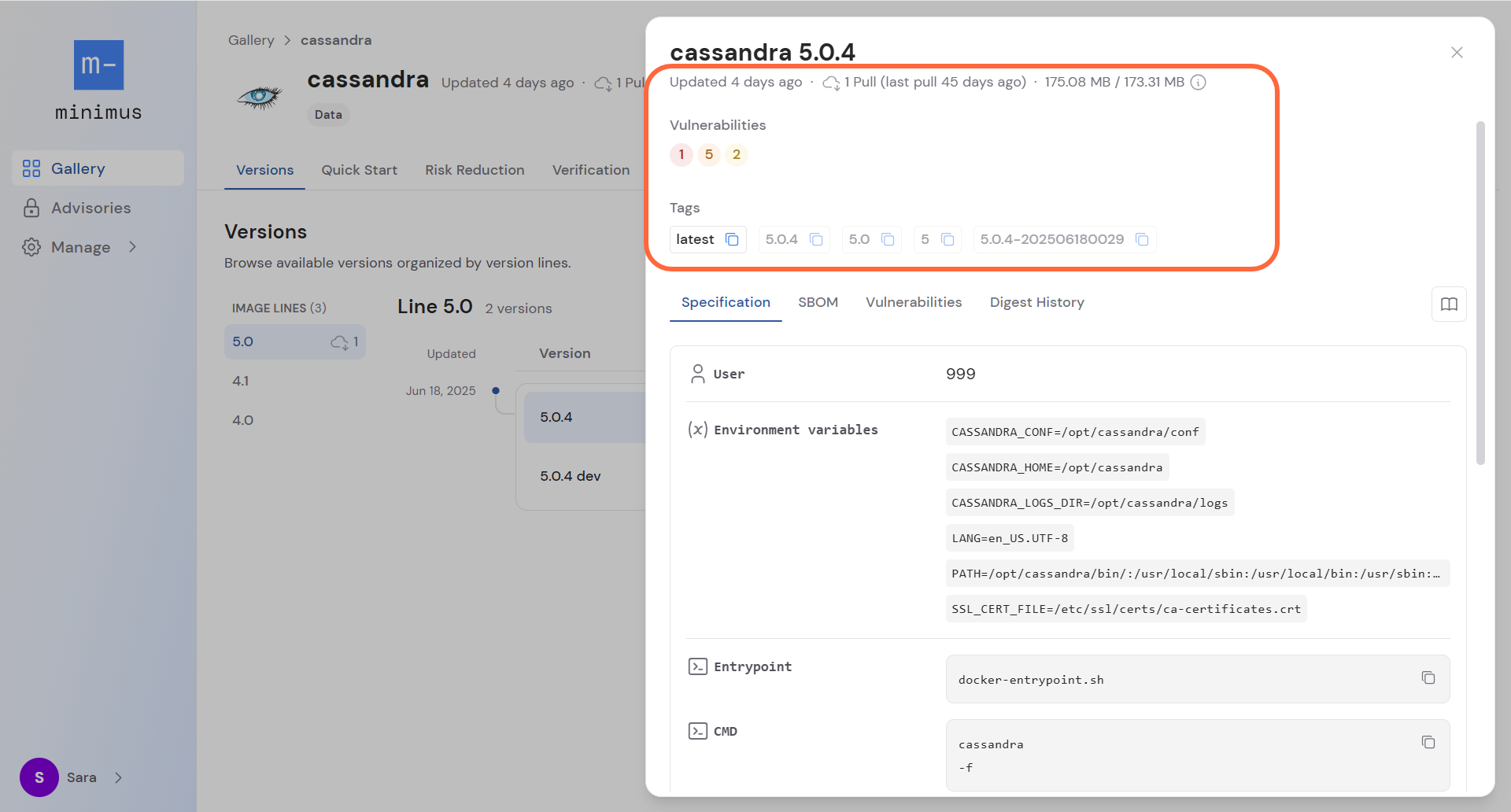
- Version metadata shows:
- When the version was last updated
- Aggregate pull stats to date showing how many times the image version was pulled by you or your organization and when it was last pulled.
- The image size for the amd64 and arm64 architectures.
- The current vulnerability status showing the number of vulnerabilities by their severity.
- The full list of tags for the image version is provided. If the image is included in your subscription, you can copy the pull commands in one-click. For example, you can copy the tag with the date stamp and active token. It will look like this:
docker pull reg.mini.dev/{token}/go:1.23.8-dev-202504210029
Tabs
Specification
The specification tab provides technical specs in a convenient format to save you time. It lists:- Default user
- Environment variables. Note that most Minimus images include the certificate variable
SSL_CERT_FILE=/etc/ssl/certs/ca-certificates.crt - Entrypoint and default command
- Default volumes
- Default working directory
- Stop signal
SBOM
The software bill of materials lists all component packages by version and license per architecture.- Toggle the view between amd64 and arm64.
- You can search the list by package name, version, and license.
- Click the Download Information button to grab the relevant Cosign command for downloading the signed SBOM. You will need Cosign and jq locally installed. About verification
Learn more about SBOMs and why SBOMs are now mandatory by executive order for all U.S. government agencies.
Download SBOM
Click the button Download Information in the SBOM tab to grab the relevant Cosign command. For example:Vulnerabilities
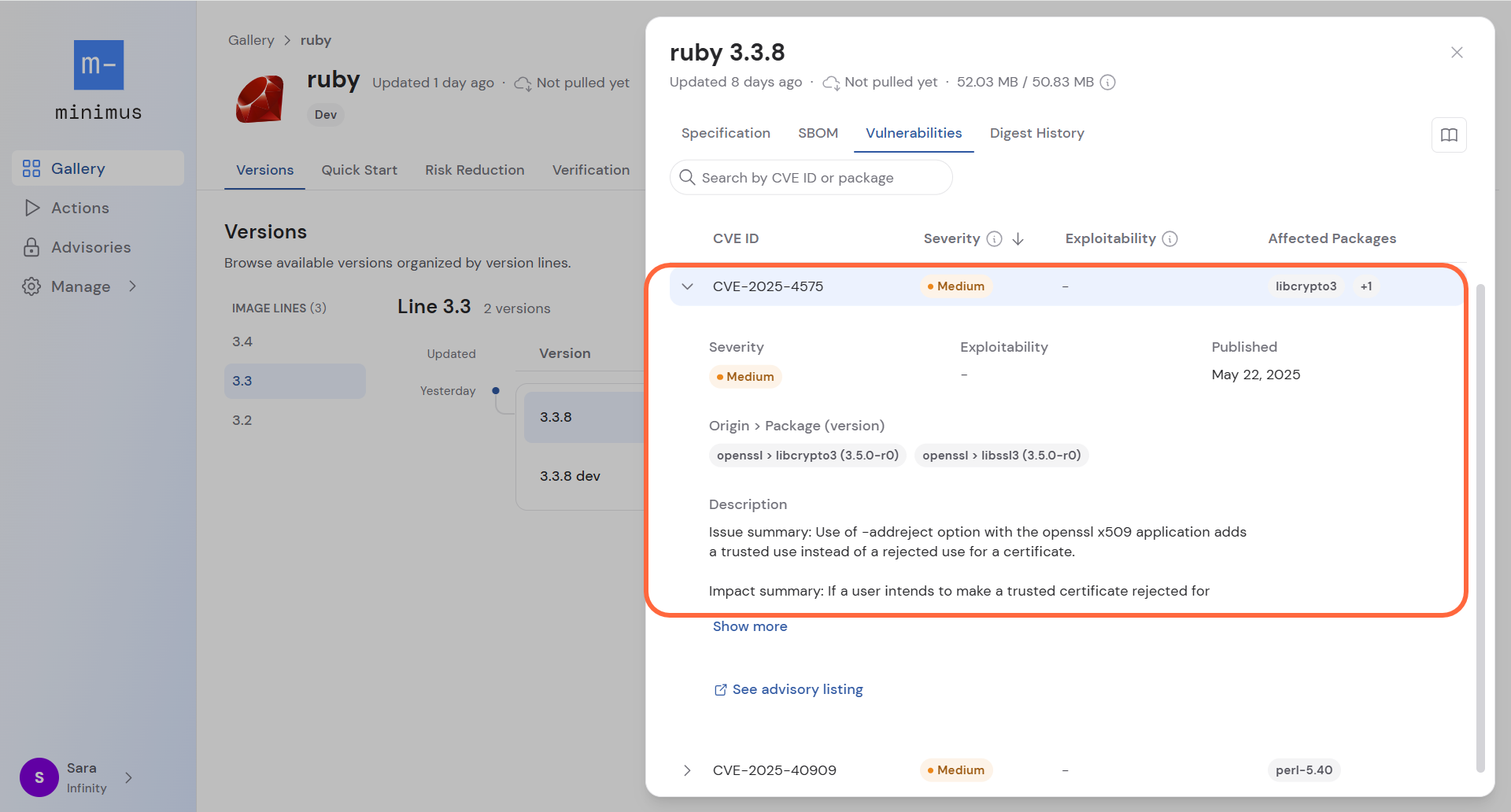
The version vulnerabilities report lists all vulnerabilities currently impacting the version, by origin package. The report is compiled from data collected from package scanners that are run on a frequent basis several times a day.- Note that the report is for the most recent build for the version. Check the Digest History tab to see if previous builds have vulnerabilities.
- You can search the list by CVE ID or package name.
- The exploitability label marks vulnerabilities at high risk:
- A vulnerability listed in the CISA KEV catalog is marked as an active exploit.
- A vulnerability with a high EPSS score (over 60%) that is not in the CISA KEV catalog is marked as a Likely exploit.
- Expand a vulnerability to see when it was published, its description, and a link to the advisory listing.
- Expand a vulnerability to see the derived package and version. For example:
Origin > Package (version)
openssl > libcrypto3 (3.5.0-r0)
Download VEX
Use the OpenVEX document to filter out false positives from vulnerability scan results. Minimus generates anopenvex.json file for each image digest. The file lists all vulnerabilities detected for that image (based on its SBOM) and their status.
A typical workflow is:
- Obtain your vulnerability scan results in SARIF format.
- Download the VEX document for the matching image digest.
-
Use
vexctlto filter the scan results using the VEX document. For example:
VEX statement Structure
VEX statements are structured as follows:- Vulnerability ID and aliases
- Product and subcomponents (affected image and origin packages and their versions)
- Status (such as
fixedornot affected) - Justification and impact statement. The justification for unaffected images is often
vulnerable_code_not_presentorcomponent_not_presentand the impact statement provides more specific details for the decision.
Example of VEX statement for CVE
Digest History
The digest history shows current and previous builds of the image version, shown with their current vulnerability count. The chronological timeline shows when every digest was published and how many vulnerabilities it currently has. It also details which build was pulled. Both the timestamp tag and its equivalent digest ID are shown. Learn more about the timestamp tag