Minimus builds its images directly from source and manages its own internal CI/CD pipelines. The following diagram describes the process.
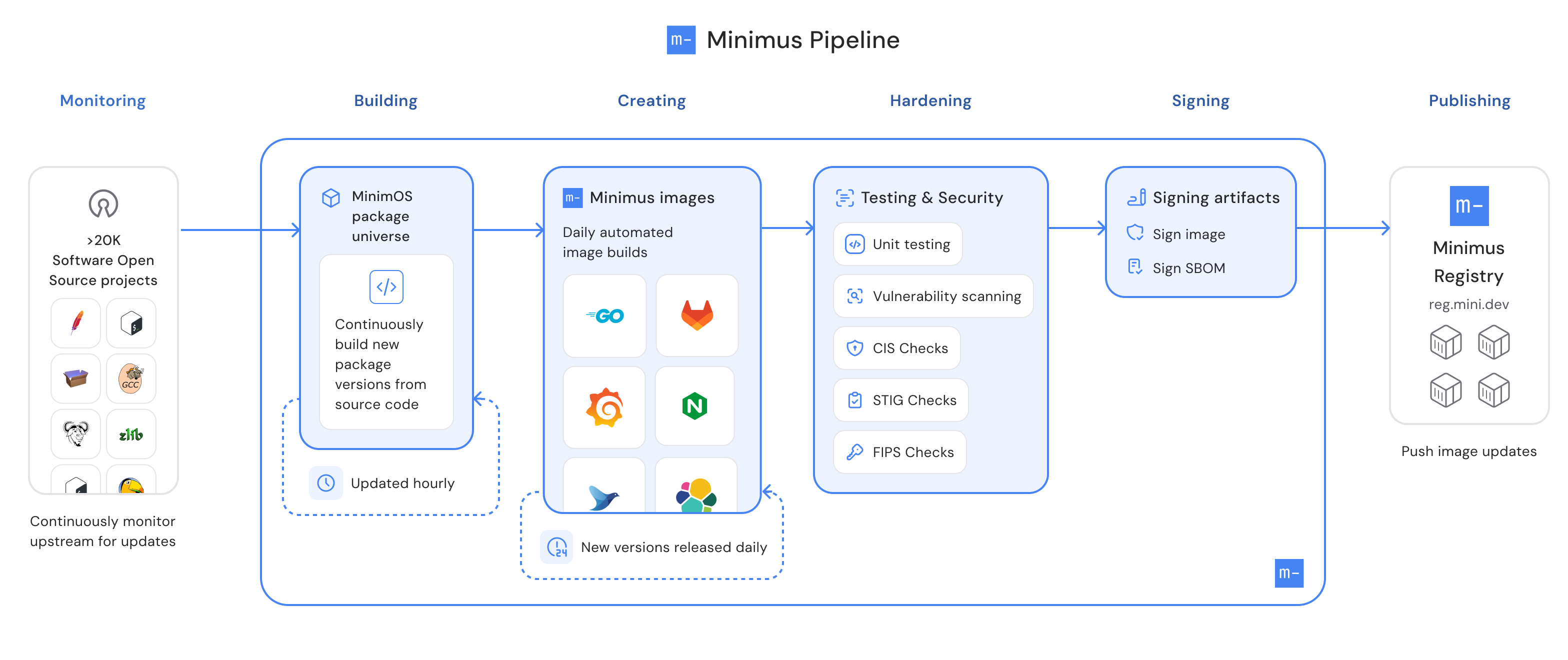
The Minimus build pipeline
Minimus monitors all upstream projects to detect updates on a continuous basis. The pipeline involves standardized build processes and automated workflows as follows:
- Minimus continuously monitors open source projects and triggers a new package build every time there is an update to a package from the package maintainers in the form of a package “release” in the upstream package source. Every package build receives a new package version. For example - the
foo package maintainers have released a new minor version - going from 1.2.3 to 1.2.4, in this case Minimus will detect the new package release and it will follow the process outlined. In a counter example, the foo source code repository has received new commits, however there is no new formal release from the maintainers, in this case Minimus will not build a new version of the foo package. For rare exceptions to this process, please see the Minimus cherry-picking policy.
- Once a day, Minimus builds every image version awaiting package updates. This ensures that new updates and vulnerability fixes are delivered daily.
- The daily image build is skipped if no package updates are available.
- Image builds take into account package version constraints.
- Minimus tests the new packages and images, and runs vulnerability scans and other compliance checks. See a discussion of the Minimus testing methodology below.
- Minimus signs images and their SBOMs and publishes them to the Minimus registry. Users are encouraged to verify Minimus images and SBOMs. See verifying images
- The Minimus Console shows current vulnerability reports for all of its images, across all available versions. To achieve this transparency, Minimus continuously scans all of its packages and image versions for new vulnerabilities. See vulnerabilities report in image card
Understanding image versioning
An image can be rebuilt without a change to the version tag. It depends on which packages were updated:
-
If the primary package was updated, the image will receive a new version tag. For example, an updated
mysql package in the MySQL image or a new elasticsearch package in the Elasticsearch image.
The primary package version matches the version tag of the image.
-
If other non-primary packages were updated, the new image will have the same version tag but a new image digest and timestamp tag. See Minimus timestamp tag and digest history
Unit testing
A daily image build and validation cycle is triggered following any change to either the configuration files or any of the included packages.
Minimus image testing is designed to test build integrity, runtime correctness, and Kubernetes readiness. Extensive unit testing is performed to ensure that the image behaves as expected before it is published to the Minimus registry. Tests are fully automated and run in a controlled environment to check that required packages are present, entrypoint behavior is as expected, environment variables and file permissions are correctly set, relevant ports are listening and/or exposed, etc.
Build integrity testing
Build integrity testing checks for SBOM completeness, image structure (tags, entrypoint, etc.) and to confirm that the builds are reproducible.
Runtime correctness
Minimus images that are not expected to be run in Kubernetes undergo testing using Docker Compose and a Python TestClient for testing Python web app endpoints directly in code without starting a web server. A Python runner is used to iterate on tested images and replace a version variable with all available version tags in a Dockerfile or directly in Docker Compose. Testing also covers multi-architecture compatibility to ensure that the images can be run in both amd64 and arm64 environments.
Kubernetes readiness
For images expected to be deployed with Kubernetes and Helm charts, additional testing procedures are in place. Tests are automated within the CI/CD pipeline so that any changes to the image trigger validation to provide fast feedback and prevent regressions.
Images expected to be deployed in Kubernetes are tested in Kubernetes using a python setup tool that configures the cluster and installs necessary services and/or images using Helm where applicable. Testing is performed with Bash and/or Python to test service functionality by running tasks in the cluster.
The Minimus advisory pipeline
Publishing package advisories
Minimus scans all of its packages for vulnerabilities every few hours. Every time a new vulnerability is detected, the vulnerability advisory is published to the Minimus advisory list and initiates the Minimus review process. About advisories
Publishing image vulnerability reports
Minimus offers an up-to-date vulnerability report for every image version in its registry. The vulnerability report for every image version is based on the SBOM and package vulnerability scans and is updated several times a day. About vulnerability reports
Minimus software supply chain security
The Minimus build environment adheres to software supply chain security practices including:
- CI/CD hardening - Minimus uses a secure build pipeline with strict access controls so all packages and images are built in a protected, trustworthy environment.
- Provenance tracking - Minimus verifies the source and authenticity of open source code used in its pipeline.
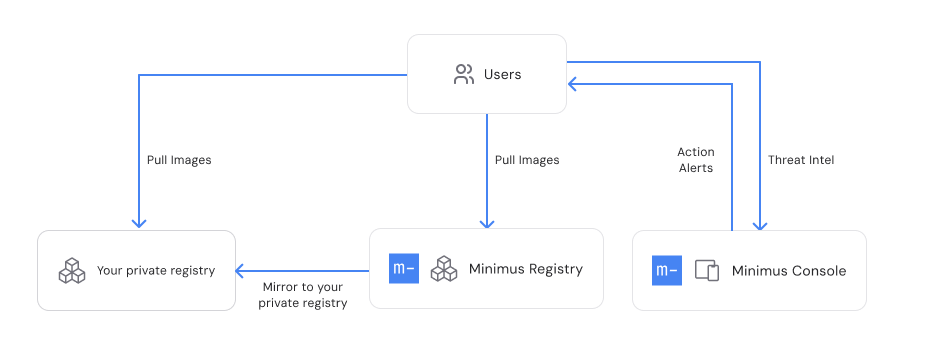
Beyond the Minimus Registry
- The user-friendly Minimus Console is your primary gateway to the Minimus Registry. Use the console to navigate the gallery of images, understand which versions are available, and learn about any new relevant threat intel and updates. About the image gallery
- You can configure Minimus actions for the registry to push alerts using dedicated webhooks. About actions
- You can also mirror images in your Minimus subscription to your private registry. About self-hosting
Last modified on February 9, 2026

